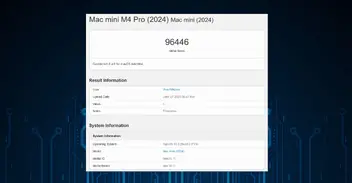
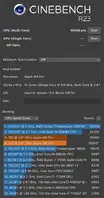
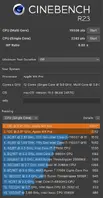
Introduction/Description
As you may know English is not our maiden language and so sorry about missing and/or wrongly used words.
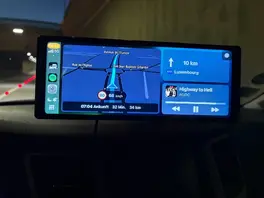
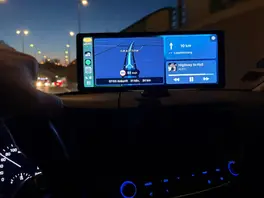
To start easy I just unboxed our iPad and put some tempered glass on it.
Photos
Ratings
These ratings are my personal opinion - Your Opinion maybe different than mine!
Display Quality
Installation Difficulty
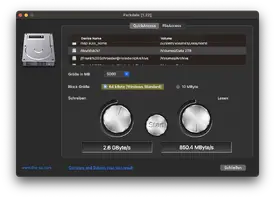
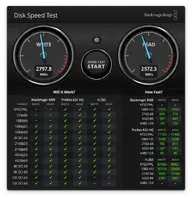
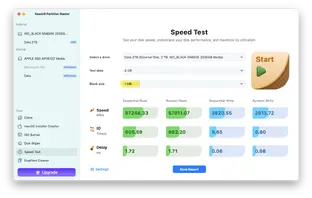
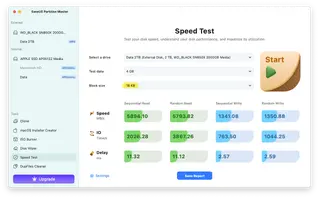
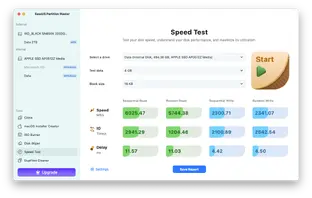
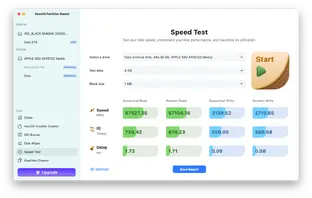
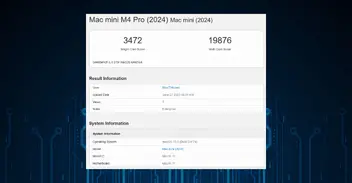
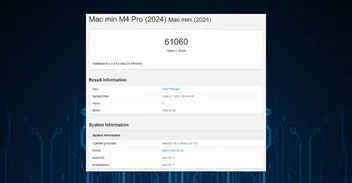
Device Speed
Handling
YouTube Video
So here is our first video in English commented video
Sorry for the sound quality - it's not the best - Next video we gonna use again our external microphones and not the one from the camera itself
Specifications
Part | Details |
|---|---|
Display | 10,9" Liquid Retina Display |
Weight | 477g |
SOC | A14 Bionic |
RAM | 4GB |
Storage | 256GB |
Back Camera | 12MP Wide camera, ƒ/1.8 aperture |
Front Camera | Landscape 12MP Ultra Wide camera |
WLAN | Wi-Fi 6 (802.11ax) with 2x2 MIMO |
Bluetooth | Bluetooth 5.2 |
Speaker | Landscape stereo speakers |
USB | USB-C |
Pen | Apple Pencil (USB-C) |
OS | iPadOS 18 |
Battery | Built‐in 28.6‐watt‐hour rechargeable lithium‑polymer battery |
Additional info | Touch ID |
Opinion
Overall I'm very satisfied with what I got for my price. I got it for 490,62€ instead of 559,44€. Unfortunately only the version without a power supply was available but I simple bought it apart.
It was also easy to put on the tempered glass and to recover the date from the old iPad was ultra easy. I think everyone can do this as it is also well explained during the setup process.
I just can always recommend an iPad if you ever need a tablet.