If you ever needed a Machine Name for an IP Address you can simply try this PowerShell command (always run as administrator).
There is an alternative to get more information while connection to the Active Directory (if available).
If you ever needed a Machine Name for an IP Address you can simply try this PowerShell command (always run as administrator).
There is an alternative to get more information while connection to the Active Directory (if available).
Here are some useful commands regarding the DNS cache, resolve etc.
#Display the DNS Cache
ipconfig /displaydns
#Empty the DNS Cache
ipconfig /flushdns
#Display DNS Cache (Powershell only)
Get-DnsClientCache
#Empty the DNS Cache (PowerShell only)
Clear-DnsClientCache
#Test a connection to a computer (ping like PowerShell command)
Test-Connection ComputerName
<# Provides information about network latency and network loss at intermediate hops between a source and destination.
This command sends multiple echo Request messages to each router between a source and destination, over a period of time, and then computes results based on the packets returned from each router.
Because this command displays the degree of packet loss at any given router or link, you can determine which routers or subnets might be having network problems. #>
pathping ComputerName
#Performs a DNS name query resolution for the specified name
Resolve-DnsName ComputerName
#Find DNS records for a specific computer
nslookup -debug ComputerNameI had recent attacks on my Linux server and so I was searching on how to add an IP drop with my firewall.
On my Sites I have a security system that blocks already many things but unfortunately not all.
And so here I show you an example on how to do it (at least how I did it).
#add the ip 91.92.252.176 to the connection reject list
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="91.92.252.176" reject'
#reload the firewall with the new settings
firewall-cmd --reload
#see the state of the firewall engine
firewall-cmd --state
#see the current settings
firewall-cmd --list-allExample - You want to add an IP that is already exisiting
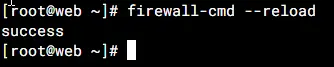
Reload firewall - if all is ok you'll get a success
![]()
Checking the state will show you if it's running or it's stopped
With list-all you gonna see the current settings - so also what is allowed (here logicaly obfuscated)
PAN
Personal Area Network A personal area network (PAN) is a computer network for interconnecting electronic devices within an individual person's workspace. A PAN provides data transmission among devices such as computers, smartphones, tablets and personal digital assistants.
LAN
Local Area Network A local area network (LAN) is a collection of devices connected together in one physical location, such as a building, office, or home.
WLAN
Wireless Local Area Network A wireless local area network (WLAN) is a network that transmits information using electromagnetic waves or light, allowing devices to connect to the internet or other devices without the need for physical cables. WLANs are commonly used for wireless internet access in homes, offices, and public places.
CAN
Campus Area Network A campus area network (CAN) is a computer network that spans a limited geographic area. CANs interconnect multiple local area networks (LAN) within an educational or corporate campus. Most CANs connect to the public Internet.
MAN
Metropolitan Area Network A metropolitan area network (MAN) is a network that covers a smaller geographical area such as a city or a large college campus system. Good examples of MANs are the local telephone company and your local cable TV company. MANs are also widely used in large companies and in governments to interconnect their computers.
WAN
Wide Area Network A wide-area network (WAN) is the technology that connects your offices, data centers, cloud applications, and cloud storage together. It is called a wide-area network because it spans beyond a single building or large campus to include multiple locations spread across a specific geographic area, or even the world.
SAN
Storage Area Network A Storage Area Network (SAN) is a network of storage devices that can be accessed by multiple servers or computers, providing a shared pool of storage space.
SANS
System Area Network A system area network (SAN) is a group of devices that are linked by a high-speed, high-performance connection. A SAN connection uses Internet Protocol (IP) addresses, which are assigned by TCP/IP to each SAN network interface controller (NIC), to determine data routing.
POLAN
Passive Optical Local Area Network A Passive Optical Network (PON) utilizes fiber-optic technology to distribute data from one source to multiple endpoints. The term "passive" denotes the use of optical fiber cables linked to an unpowered splitter, which transmits data from the service provider's network to numerous customers.
EPAN
Enterprise Private Network An Enterprise Private Network (EPN) is a computer network built by a business to interconnect its various company sites such as production sites, offices, and shops. This private network allows companies to share resources and communicate effectively.
VPN
Virtual Private Network A VPN protects its users by encrypting their data and masking their IP addresses. This hides their browsing activity, identity, and location, allowing for greater privacy and autonomy. Anyone seeking a safer, freer, and more secure online experience could benefit from a VPN.
Virtual Private Network - VPN
Cloud Based Security Brokers - CASB
Antivirus / Antimalware
I personally recommend to just use the Microsoft Defender
Endpoint Detection and Reponse (EDR)
Firewalls
Identity and Access Management (IAM)
Intrusion Detection and Prevention Systems (IDPS)
Security Information and Event Management (SIEM)
Secure Web Gateways (SWG)
Network Access Control (NAC)
Email Security
Data Loss Prevention (DLP)
These ratings are my personal opinion - Your Opinion maybe different than mine!
Graphics
Difficulty
Steam Deck
ROG Ally - Bazzite
Vessel of Hatred is a paid expansion for Diablo 4 that comes with new ways to play and new evils to vanquish. Players get to choose whether they want to continue playing the base game of Diablo 4 or purchase the expansion and experience its contents.
EMBRACE THE SHADOWS!
A new region of Hell is coming to Diablo IV on October 8 - 2024! Vessel of Hatred is the first expansion and next chapter of the genre-defining, award-winning series by Blizzard Entertainment. Pre-purchase now for immediate access to in-game rewards and prepare for the darkness that awaits you as the first expansion charges through the land of Sanctuary.
NEW CLASS: SPRIRITBORN
Ranked among the apex predators of the jungle, the Spiritborn is an entirely new class to the Diablo series. They are battle-hardened with mystical synergies that could only be awakened deep within the jungles of Nahantu. Become one of the Spiritborn and embrace the ethereal Spirits entwined with this ancient civilization.
NEW REGION: NAHANTU
Explore Nahantu, the new jungle region in Diablo IV full of secrets, dangerous new Dungeons, Strongholds, and ferocious demons from warring Tribes.
CONTINUE THE CAMPAIGN
Set immediately following the events of Diablo IV, Vessel of Hatred continues the dark story as you fight to save Neyrelle from Mephisto's tightening grip on her soul, still reeling from the choice she made to contain him. The search for Neyrelle takes you deep into the ancient jungle as she grapples with the imprisoned Prime Evil. Attempt to unravel Mephisto’s dark plot while new foes encircle your every move, planning your demise. The fate of Neyrelle’s soul - and her ability to stop this Prime Evil from destroying Sanctuary - rests in your hands.
Never fight alone as new Mercenaries can join you on your quest to fight in the dense undergrowth of Nahantu and beyond. These powerful allies grow in power as they progress, and each are equipped with unique abilities to help you in combat.
NEW GAME UPDATES
Vessel of Hatred also has huge updates for all Diablo IV players with new class skills, paragon boards, legendary glyphs, dungeon types, Tree of Whispers activities, and more.
A new co-op PvE mode where you work with your friends to complete objectives and slay the boss in a multi-level dungeon, while getting loot and rewards.
As I can't play daily it always take some time until I finish my test but what should I say? I simply love Diablo IV as I loved the Diablo games before.
The new class is great as also the new area.
The story continues which is great and it take several hours to finish it but there is such abrupt ending...
I thought it would continue but it was the end and so we can say the next DLC will come with the continuing story...
For end gaming content I'm not the one to ask - here you need to ask people that don't have any life and play daily for hours and hours.
But I would always recommend this game 🙂
Minimum
Operating System (OS) | Windows 10 64Bit (1909 or higher) |
Processor (CPU) | Intel Core i5-2500K |
Memory (RAM) | 8 GB |
Graphics processing unit (GPU) | Nvidia Geforce GTX 660 |
DirectX | 12 |
Network | Broadband internet connection |
Disk Space | 90 GB |
Additional Comment | 1080p native resolution |
Recommended
Operating System (OS) | Windows 10 64Bit (1909 or higher) |
Processor (CPU) | Intel Core i5-4670K |
Memory (RAM) | 16 GB |
Graphics processing unit (GPU) | Nvidia GTX 970 |
DirectX | 12 |
Network | Broadband internet connection |
Disk Space | 90 GB |
Additional Comment | 1080p resolution |
There are some default Ports used when working on a network/server but most of these ports exists in a default way and a secure way. Here are some essential ports listed with it's default number and it's secured number.
Insecure Port | Protocol | Description | Secure Port | Protocol | Description |
|---|---|---|---|---|---|
21 | FTP | File Transfer Protocol (FTP) sends the username and password using plaintext from the client to the server. | 22 | SFTP | Uses encryption to protect the user credentials and packet of data being transferred. |
23 | Telnet | All information to & from the host on a telnet connection is sent in plaintext & cand be intercepted by an attacker. | 22 | Secure Shell | Secure Shell (SSH) on port 22 uses encryption to ensure that traffic between the host and terminal is not sent in plaintext format. |
25 | SMTP | Simple Mail Transfer Protocol (SMTP) is the default for sending email messages. Since it is unencrypted, data contained within the emails could be discovered by network sniffing. | 587 | SMTP | The secure alternative is to use port 587 for SMTP using Transport Layer Security (TLS) which will encrypt the data between the mail client and the mail server. |
37 | Time | Time Protocol may be in use by legacy equipment and has mostly been replaced by using port 123 for Network Time Protocol (NTP). | 123 | NTP | NTP on port 123 offers between errorhandling capabilities, which reduces the likelihood of unexpected errors. |
53 | DNS | Domain Name Service (DNS) is still used widely. | 853 | DoT | However using DNS over TLS (DoT) on port 853 protects DNS information from being modified in transit. |
80 | HTTP | Hyper Text Transfer Protocol (HTTP) is the basis of nearly all web browser traffic on the internet. Information sent via HTTP is not encrypted and is susceptible to sniffing attacks. | 443 | HTTPS | HTTPS using TLS encryption is preferred as it protects the data in transit between the server and the browser. |
143 | IMAP | Internet Message Access Protocol (IMAP) is a protocol used for retrieving emails. IMAP traffic on port 142 is not encrypted and susceptible to network sniffing. | 993 | IMAP | The secure alterative is to use port 993 for IMAP which adds SSL/TLS security to encrypt the data between the mail client and the mail server. |
445 | SMB | Server Message Block (SMB) is used by many versions of Windows for accessing files over the network. Files are transmitted unencrypted. | 2049 | NFS | Network File System (NFS). Although NDS can use encryption it is recommended that NFS not be allowed through firewalls either. |
389 | LDAP | Lightweight Directory Access Portocol (LDAP) is used to communicate directory information from servers to clients. Since LDAP is not encrpyted it is susceptible to sniffing and manipulation attacks. | 636 | LDAPS | Lightweight Directory Access Portocol Secure (LDAPS) adds SSL/TLS LDAPS Security to protect the information while it is in transit. |
Within the network there are many different protocols.
9 of them are more than essential.
Short Name | Long Name | Description |
|---|---|---|
HTTP | Hypertext Transfer Protocol | This is how web pages are requested and delivered on the internet. |
HTTPS | Hypertext Transfer Protocol Secure | It's like HTTP but with added security for safer data transfer. |
FTP | File Transfer Protocol | It's used to send and receive files over the internet. |
TCP | Transmission Control Protocol | It ensures that data sent over the internet arrives intact. |
IP | Internet Protocol | It provides addresses for devices on the internet. |
UDP | User Datagram Protocol | It's like TCP but faster and less concerned with data integrity. |
SMTP | Simple Mail Transfer Protocol | It's used for sending emails between servers. |
SSH | Secure Shell | It's a secure way to access and control remote computers. |
IMAP | Internet Message Access Protocol | Allow users to access email messages stored on a remote mail server. |
No. | Layer | Description | Device | Implementations |
|---|---|---|---|---|
7 | Application | Provides services directly to user applications. | Gateway | SMB |
6 | Presentation | Performs data transformations and services including formatting, compression and encryption services to provide a common interface for user applications. | Gateway | HTTP |
5 | Session | Establishes, manages and terminates connections between applications at each end. | Gateway | NetBEUI |
4 | Transport | Provides transparent transfer of data between end systems by insulating layers 5-7 from complexities of layers 1-3. | Gateway | IP |
3 | Network | Establishes, maintains and terminates network connections. | Router | IP |
2 | Data Link | Divided into two sub-layers: | Switch | Ethernet |
1 | Physical | Controls transmission of the bit stream data over the physical medium. | Multiplexer | Ethernet |
The OSI Layer should be commonly known in the world of ICT but did you know what attack targets what layer?
Here a table to clarify this...
| Layers | Attacks | |
|---|---|---|
| 7 | Application | Exploit |
| 6 | Presentation | Phishing |
| 5 | Session | Hijacking XSS Attacks / Sessions Side Jacking / Malware |
| 4 | Transport | Reconnaissance / DoS (Denial-of-Service) TCP Session Hijack / Fraggle / Syn Flood / Land Attacks |
| 3 | Network | Man in the Middle Smurf Attack / Ping of Death / Teardrop |
| 2 | Data Link | Spoofing MAC Spoofing / MAC Flooding / VLAN Hopping |
| 1 | Physical | Sniffing |
Information and communications technology (ICT) is an extensional term for information technology (IT) that stresses the role of unified communications and the integration of telecommunications (telephone lines and wireless signals) and computers, as well as necessary enterprise software, middleware, storage and audiovisual, that enable users to access, store, transmit, understand and manipulate information.
ICT is also used to refer to the convergence of audiovisuals and telephone networks with computer networks through a single cabling or link system. There are large economic incentives to merge the telephone networks with the computer network system using a single unified system of cabling, signal distribution, and management. ICT is an umbrella term that includes any communication device, encompassing radio, television, cell phones, computer and network hardware, satellite systems and so on, as well as the various services and appliances with them such as video conferencing and distance learning. ICT also includes analog technology, such as paper communication, and any mode that transmits communication.
ICT is a broad subject and the concepts are evolving. It covers any product that will store, retrieve, manipulate, process, transmit, or receive information electronically in a digital form (e.g., personal computers including smartphones, digital television, email, or robots). Skills Framework for the Information Age is one of many models for describing and managing competencies for ICT professionals in the 21st century.

